API Settings
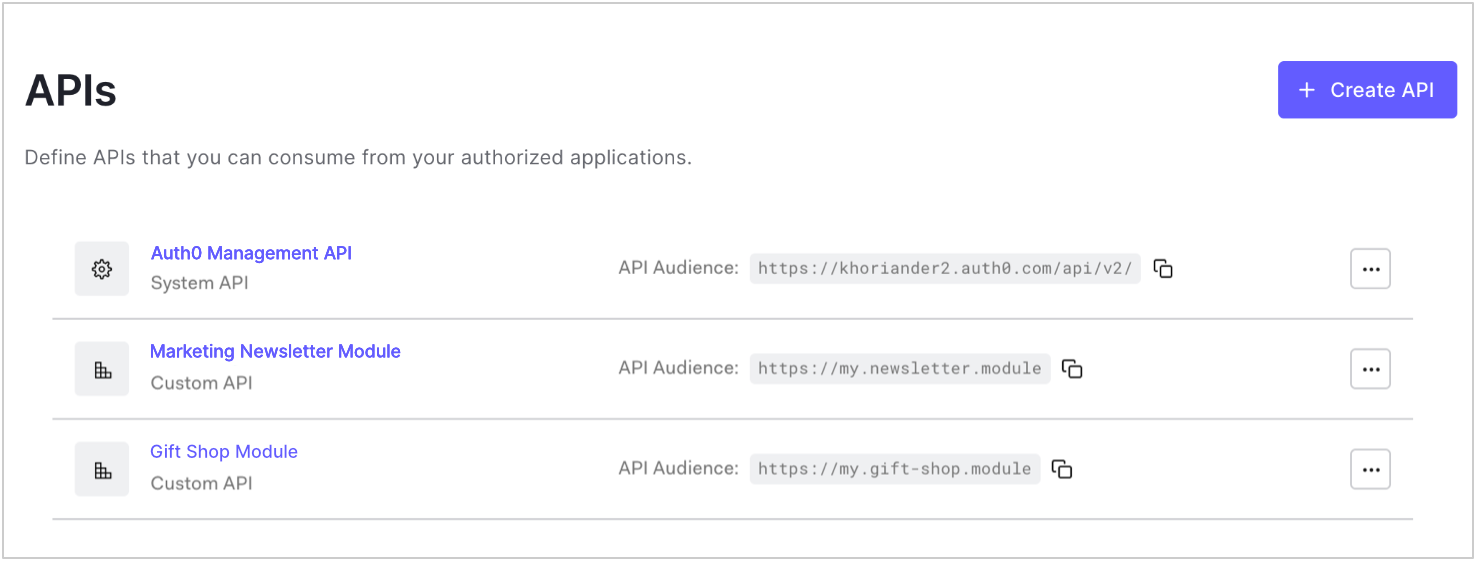
Use the Settings tab in the Auth0 Dashboard at Dashboard > Applications > APIs to configure registered APIs that you can consume from your authorized applications. To configure an API's settings, click ... next to an API in the list and select Settings or click the API name. To learn how to create and register an API, read Register APIs.
Settings
Use the settings on this tab to configure token expiration, role-based access control (RBAC), and other access settings. Click Save at the bottom of the tab to save changes.
General Settings
These fields were set when you initially registered the API, except in the case of the Auth0 Management API. You can only modify the Name.
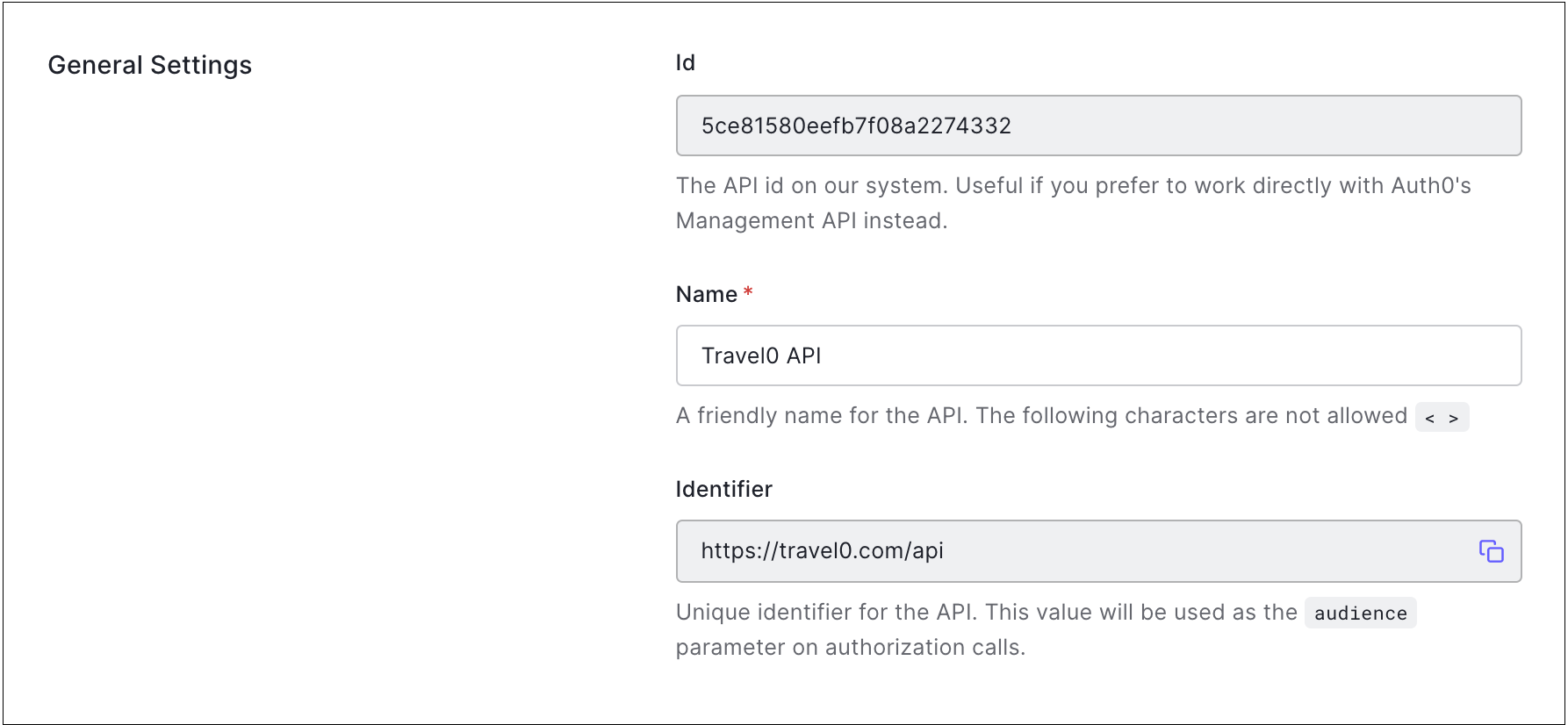
Id: A unique alphanumeric string generated by Auth0. This information is read-only, and you will only need it if you will be working directly with Auth0's Management API Resource Servers endpoints.
Name: A friendly name for the API. Does not affect any functionality. The following characters are not allowed:
< >.Identifier: A unique identifier for your API. This value is set upon API creation and cannot be modified afterward. We recommend using a URL, but this doesn't have to be a publicly available URL; Auth0 will not call your API at all.
Token Settings
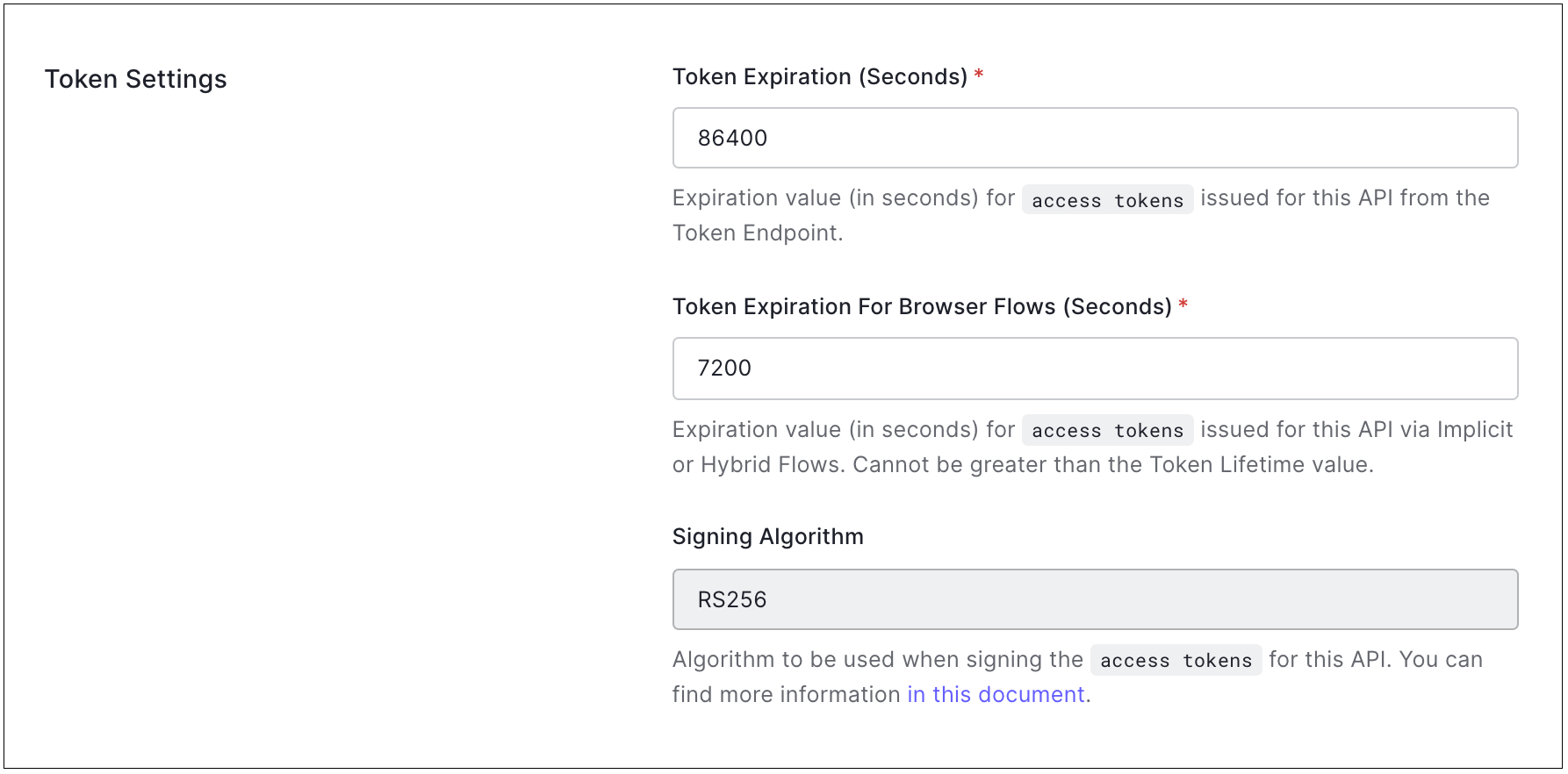
Token Expiration (Seconds): The amount of time (in seconds) before the Auth0 Access Token expires. The default value is 86400 seconds (24 hours). The maximum value you can set is 2592000 seconds (30 days).
Allow Skipping User Consent: When this is enabled, the User Consent dialog will not be shown to the end-user when a first-party application requests authorized access against your API. Please note that if the hostname of your application's callbackURL is
localhostor127.0.0.1, the consent dialog will always be displayed.Signing Algorithm: The algorithm with which to sign the tokens. The signature is used to verify that the sender of the JWT is who it says it is and to ensure that the message wasn't changed along the way. The available values are HS256 and RS256. When selecting
RS256(recommended), the token will be signed with your tenant's private key. This value is set when your API is created and cannot be modified afterward. To learn more about signing algorithms and how they work in Auth0, read Signing Algorithms.
RBAC Settings
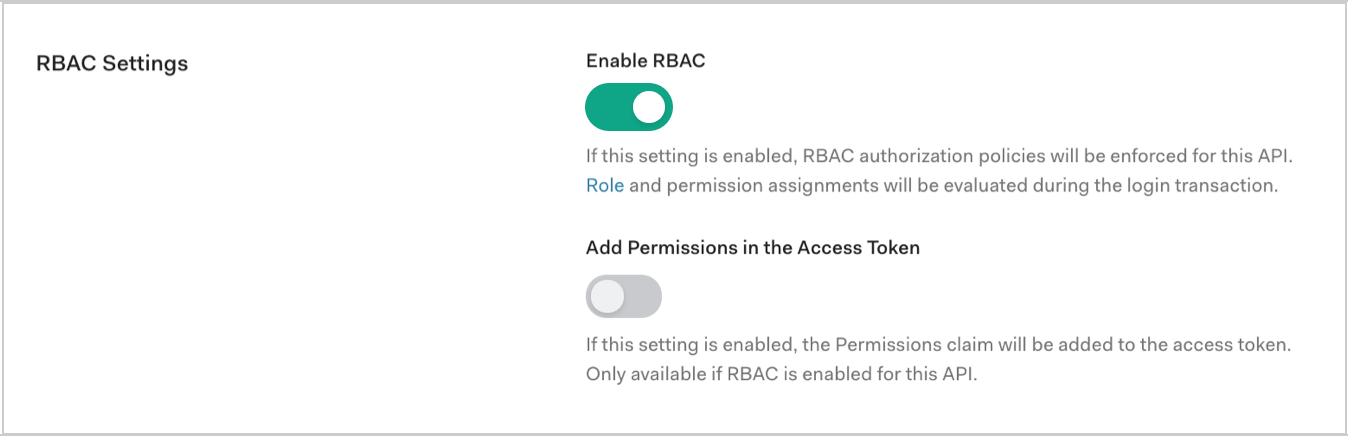
Enable RBAC: Enable this setting for RBAC policies to be enforced for the API. To learn more, read Role-Based Access Control and Enable Role-Based Access Control for APIs. For troubleshooting help, review Troubleshoot Role-Based Access Control and Authorization.
Add Permissions in the Access Token: Enable this setting to add the Permissions claim to the access token. This setting is only available if you enable RBAC. You can configure permissions on the Permissions tab.
Access Settings
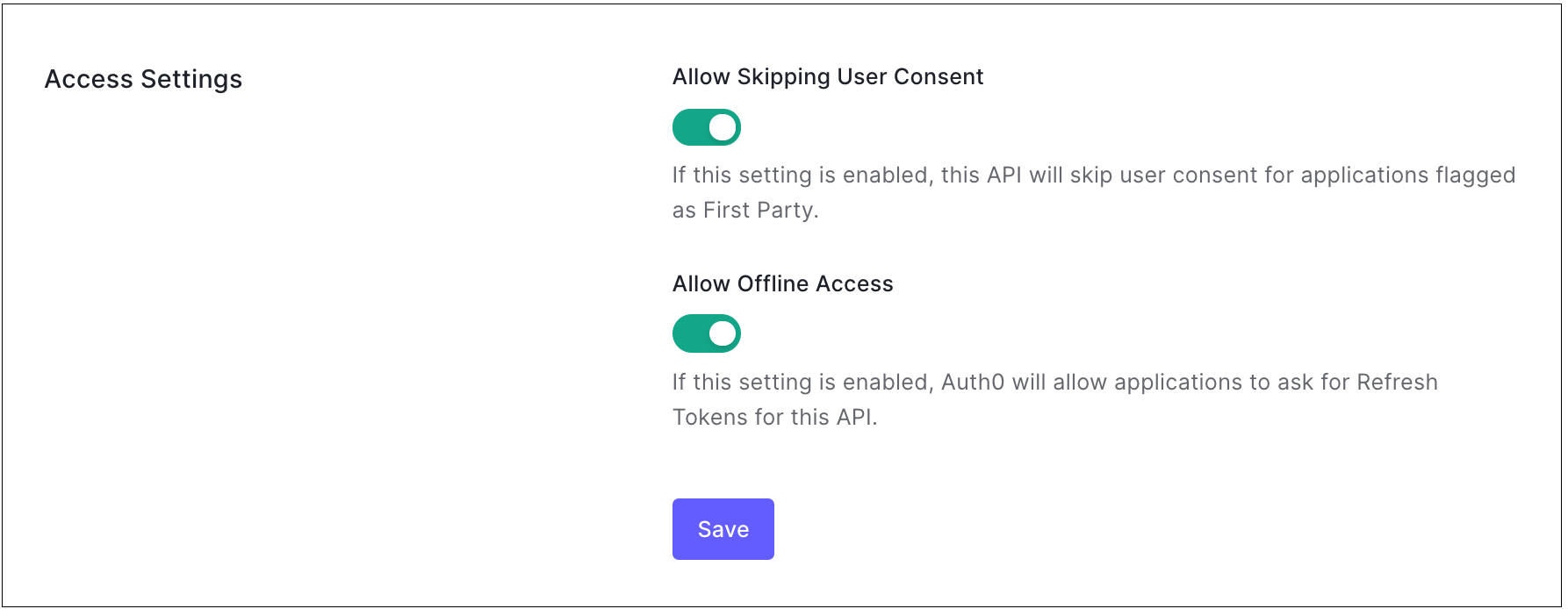
Allow Skipping User Consent: Enable this setting for the API to skip user consent for applications flagged as "first party."
Allow Offline Access: Enable this setting to allow applications to ask for refresh tokens for the API.
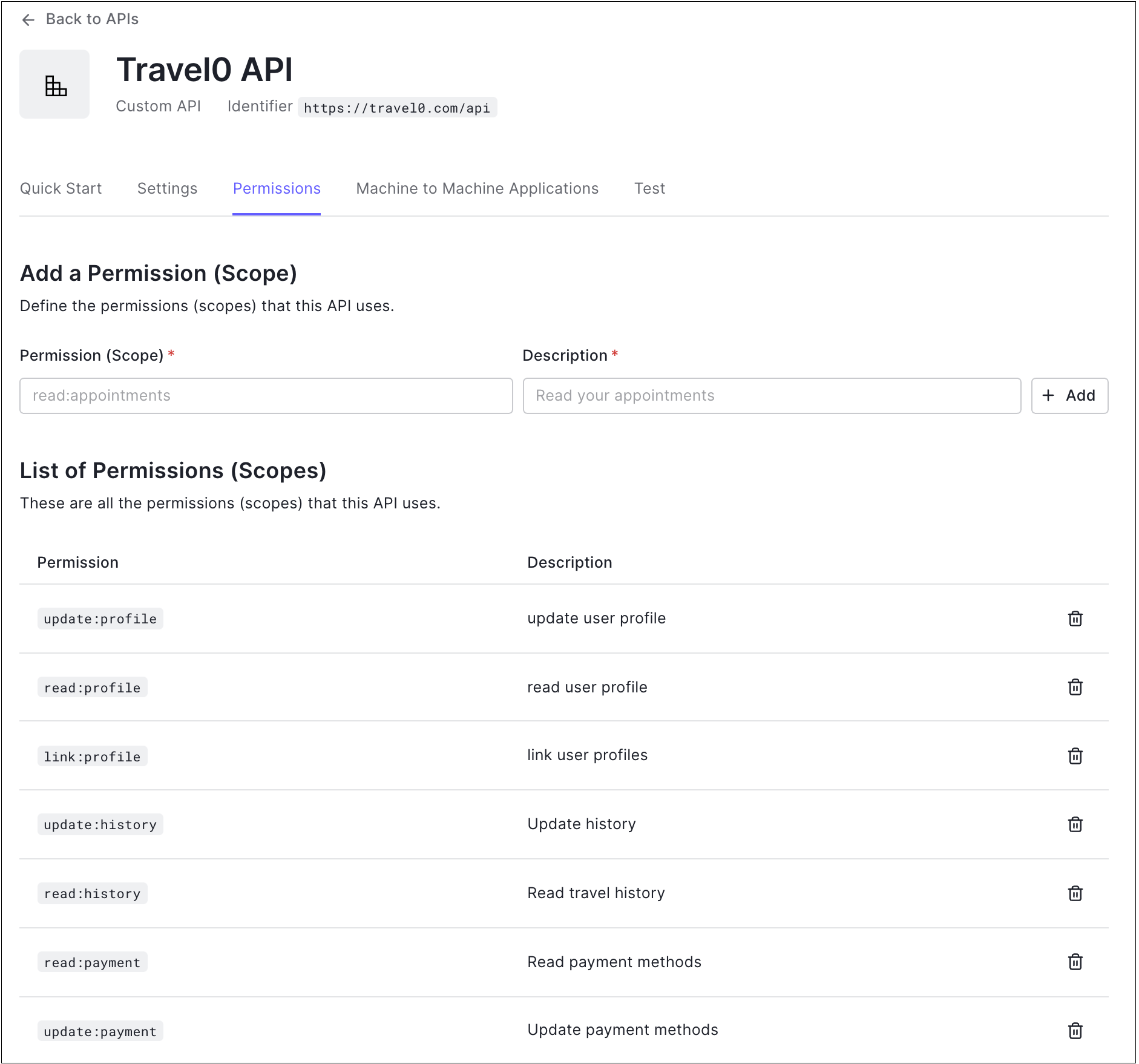
Permissions
Use the settings on the Permissions tab to define the permissions (scopes) that the API will use. To learn more, read Add API Permissions and Delete API Permissions.
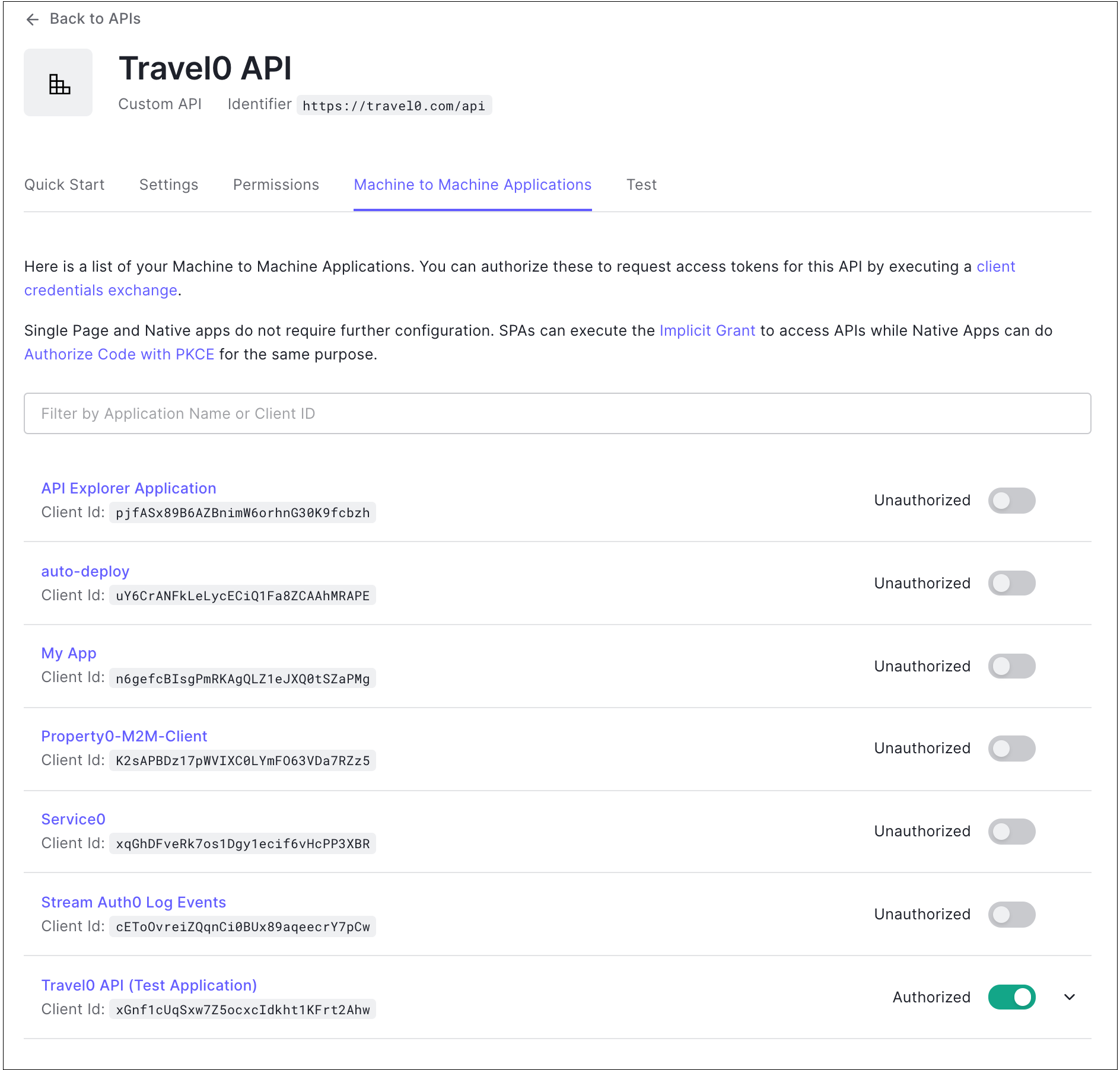
Machine-to-Machine Applications
If you have machine-to-machine applications, they will appear in a list on this tab. Use the toggles to authorize applications in the list. To learn more, read Register Machine-to-Machine Applications.
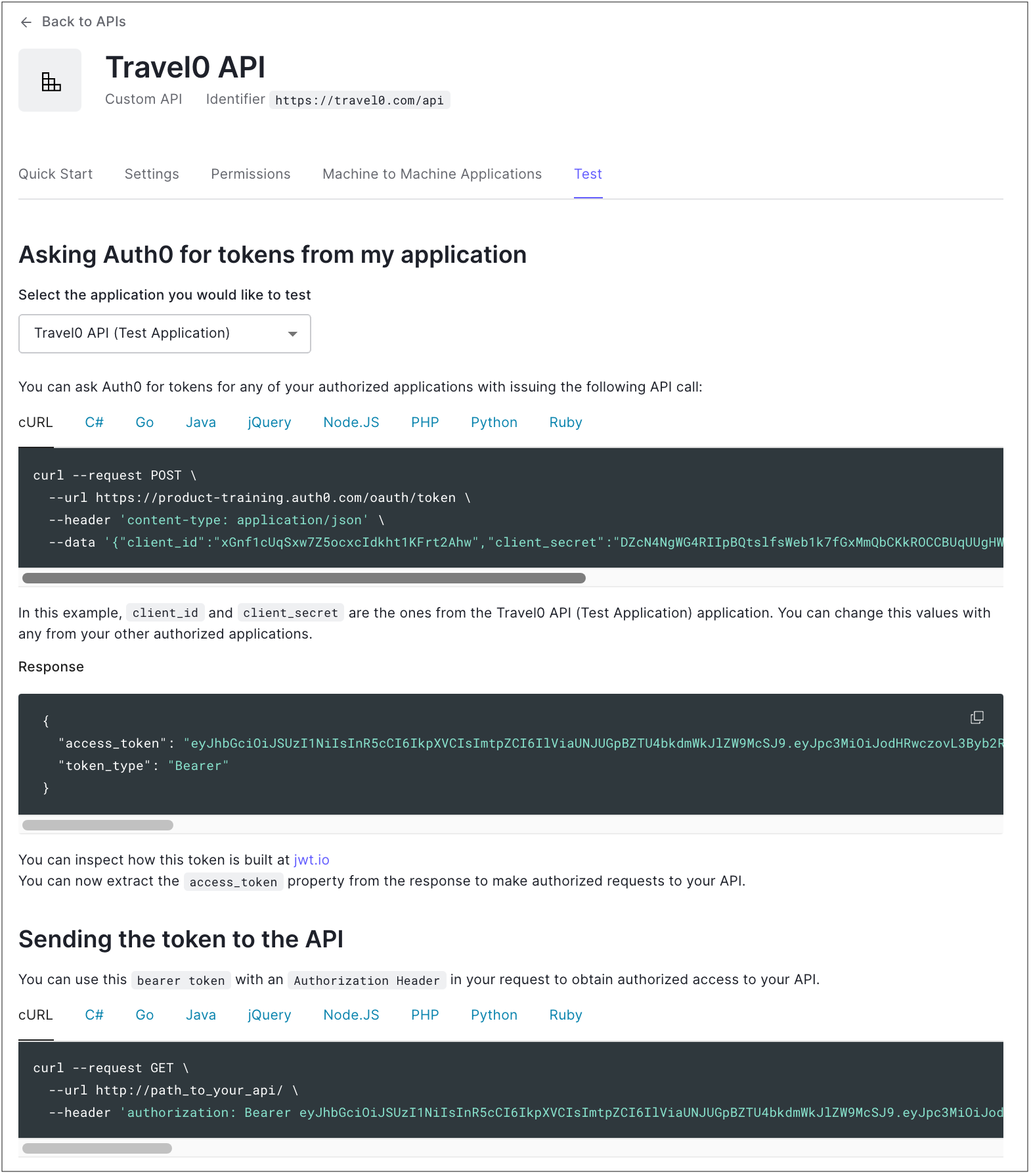
Test
You can choose an application to test with the API. To learn how to create a test machine-to-machine application for Management API testing, read Create Machine-to-Machine Applications for Testing.
Management API Explorer
If you view the Settings for the Auth0 Management API, you will see an additional tab called API Explorer.
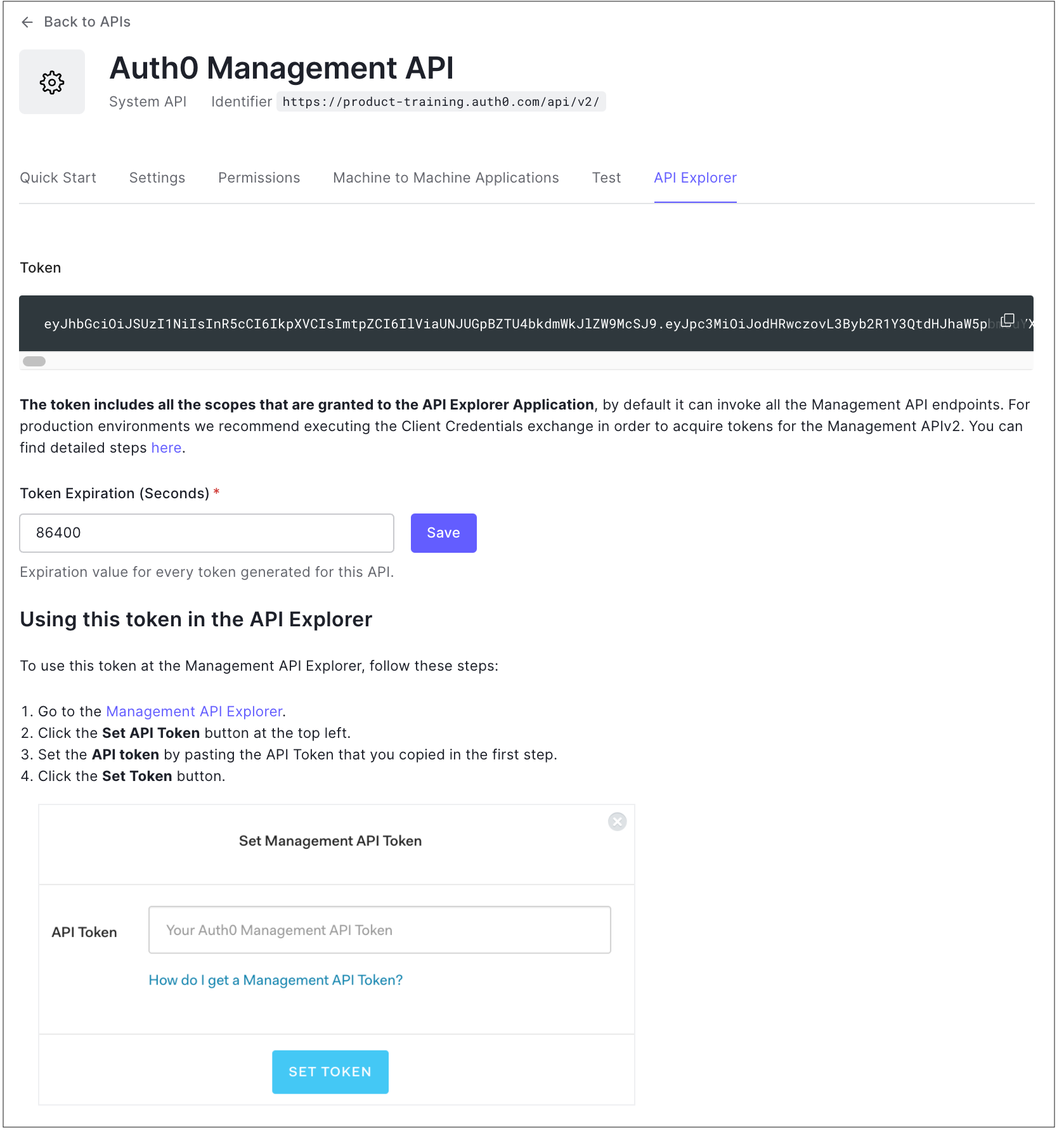
For troubleshooting help, review Check API Calls.