Resource Owner Password Flow
Though we do not recommend it, highly-trusted applications can use the Resource Owner Password Flow (defined in OAuth 2.0 RFC 6749, section 4.3), which requests that users provide credentials (username and password), typically using an interactive form. Because credentials are sent to the backend and can be stored for future use before being exchanged for an Access Token, it is imperative that the application is absolutely trusted with this information.
Even if this condition is met, the Resource Owner Password Flow should only be used when redirect-based flows (like the Authorization Code Flow) cannot be used.
How it works
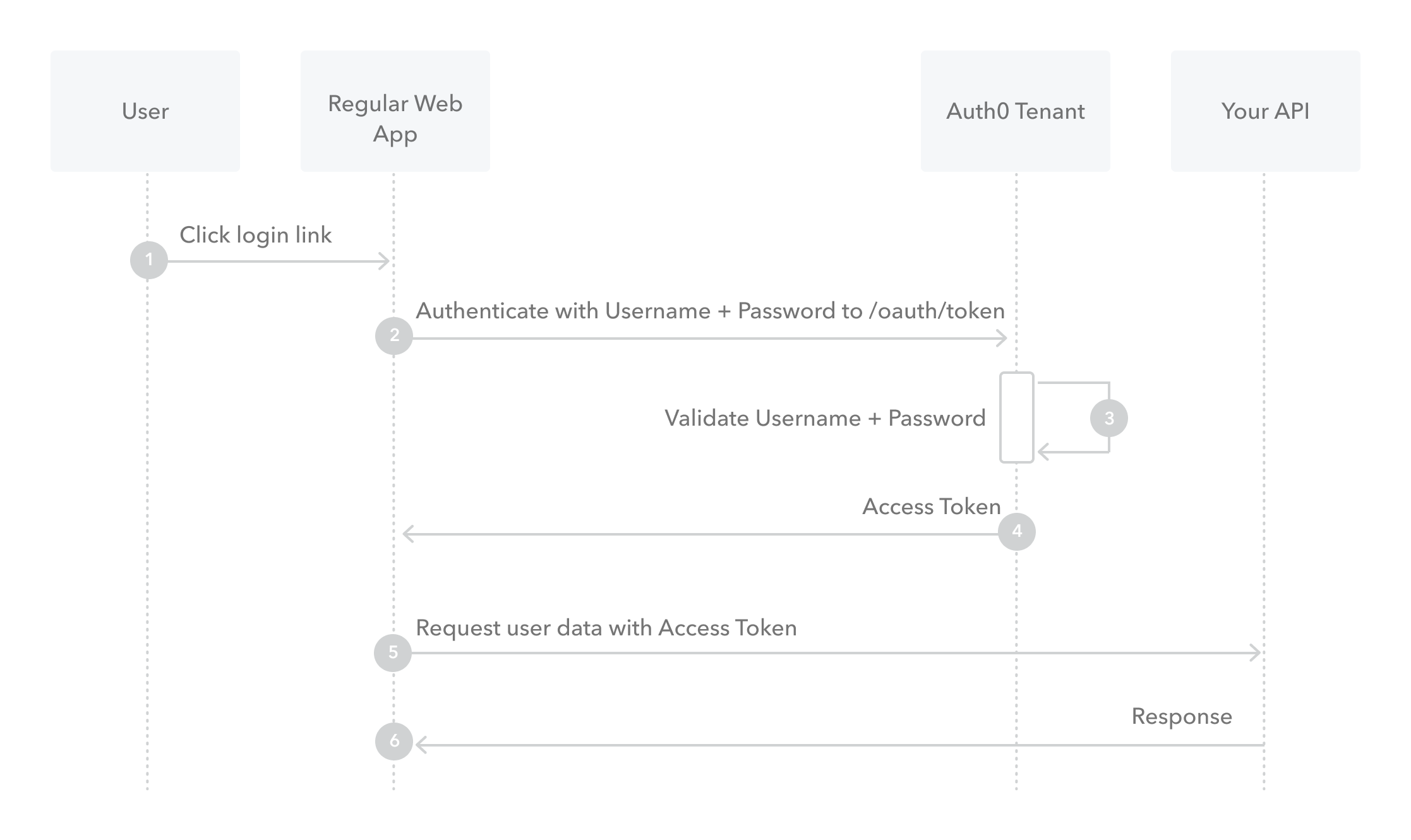
The user clicks Login within the application and enters their credentials.
Your application forwards the user's credentials to your Auth0 Authorization Server (
/oauth/tokenendpoint).Your Auth0 Authorization Server validates the credentials.
Your Auth0 Authorization Server responds with an Access Token (and optionally, a Refresh Token).
Your application can use the Access Token to call an API to access information about the user.
The API responds with requested data.
How to implement it
The easiest way to implement the Resource Owner Password Flow is to follow our tutorial to use our API endpoints to Call Your API Using the Resource Owner Password Flow.
Realm support
Auth0 provides an extension grant that offers similar functionality to the Resource Owner Password grant, but allows you to keep separate user directories (which map to separate connections) and specify which one to use during the flow.
For example, let's say you want to present a dropdown on your application's login user interface that allows users to choose their user type: Employees or Customers. In this case, you would configure Employees and Customers as realms (and set up a corresponding connection for each), which allows employee and customer credentials to be kept in separate user directories. When you request a token, you will submit the realm value along with the user's credentials and the submitted realm will be used to verify the password.
To learn more about implementing this extension grant, read Call Your API Using Resource Owner Password Flow: Configure Realm Support.
Rules
Rules will run for the Resource Owner Password Flow (including the Realm extension grant). However, redirect rules won't work. If you try to perform a redirect by specifying context.redirect in your rule, the authentication flow will return an error. To learn more about rules, read Auth0 Rules. To learn more about redirect rules, read Redirect Users from Within Rules.
MFA support
If you need to use the Resource Owner Password Flow, but require stronger authentication, you can add multi-factor authentication (MFA). To learn how, read Authenticate Using the Resource Owner Password Flow with MFA.
Attack protection
When using the Resource Owner Password Flow with brute-force protection, some attack protection features may fail. Some common issues, however, can be avoided. To learn more, read Avoid Common Issues with Resource Owner Password Flow and Attack Protection.