Bot Detection
Bot detection mitigates scripted attacks by detecting when a request is likely to be coming from a bot. These types of attacks are sometimes called credential stuffing attacks or list validation attacks. It provides protection against certain attacks that adds very little friction to legitimate users. When such an attack is detected, it displays a CAPTCHA step in the login experience to eliminate bot and scripted traffic.
To learn more, read our Credential Stuffing Attacks: What Are They and How to Combat Them whitepaper.
Auth0 uses a large amount of data and statistical models to identify patterns that signal when bursts of login/signup traffic are likely to be from a bot or script. Users who attempt to log in or create accounts from IPs that are determined to have a high likelihood of being part of a credential stuffing attack will see a CAPTCHA step. The triggers are designed so that this only happens for bad traffic; the objective is to not add friction to legitimate users.
Prerequisites
If you want to use Google reCAPTCHA Enterprise, you will need to obtain the Site Key, API Key, and Project ID from Google. To learn more, read Configure reCAPTCHA Enterprise on Google Cloud Platform.
Configure bot detection
This protection is enabled by default for all connections.
Go to Dashboard > Security > Attack Protection and select Bot Detection.
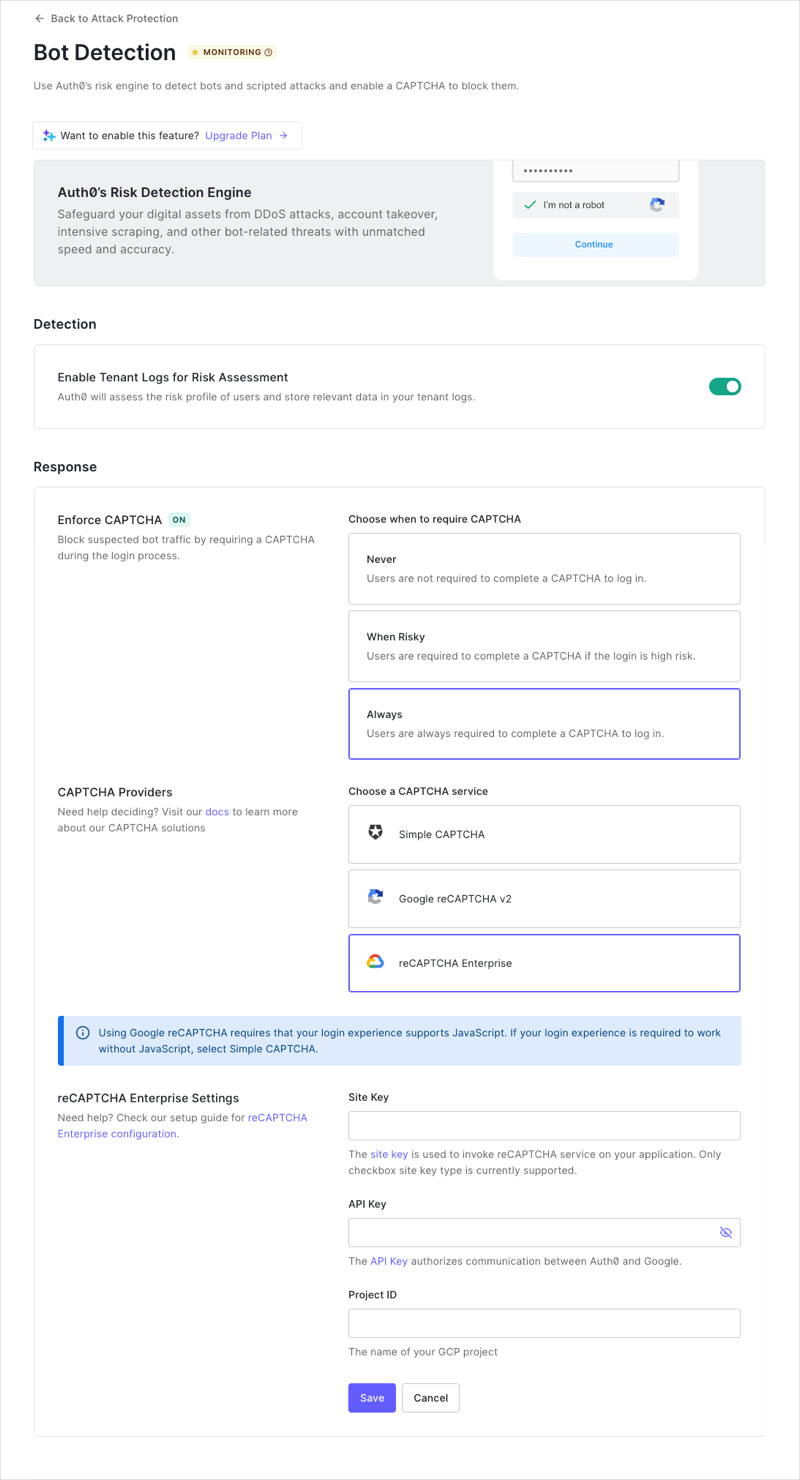
In the Detection section, enable the toggle.
In the Response section, choose when you want to require CAPTCHA.
Choose Never to never require your users to complete a CAPTCHA to log in.
Choose When Risky to only require your users to complete a CAPTCHA if the login appears to be high risk. Select the type of CAPTCHA in the next step.
Choose Always to always require your users to complete a CAPTCHA to log in. Select the type of CAPTCHA in the next step.
Choose whether you wish to use simple CAPTCHA provided by Auth0 or Google reCAPTCHA (requires external setup and registration).
If you choose Simple CAPTCHA, you are done. Choose this option if your login experience is required to work without JavaScript.
If you choose Google reCAPTCHA v2, enter the Site Key and Site Secret that you obtained when you registered your app with Google.
If you choose Google reCAPTCHA Enterprise, enter the Site Key, API Key, and Project ID that you obtained when you configured Google reCAPTCHA Enterprise on the Google Cloud Platform. To learn more, read Configure reCAPTCHA Enterprise on Google Cloud Platform.
Ensure that you have chosen When Risky or Always under Enforce CAPTCHA above.
Click Save.
Let trusted IP addresses bypass bot detection
You can make up to 100 certain IP addresses exempt from bot detection by adding them to the IP Allow List. Auth0 does not block or alert when these IPs bypass Bot Protection.
Go to Dashboard > Security > Attack Protection, and select Bot Detection.
In the IP AllowList box, type the IP addresses and/or CIDR ranges (IPv4 or IPv6) you want to allow unlimited login and signup attempts. Separate multiple addresses or ranges with commas.
Restrictions and limitations
Flow limitations
Bot protection works for web and mobile apps that use Auth0 Universal Login. For experiences that do not use Universal Login, levels of support are limited, in particular for flows that cannot support a CAPTCHA or reCAPTCHA challenge. Please ensure all of your login experiences are supported before turning on this feature, or you may introduce errors into your application.
| Flow | Limitation |
|---|---|
| New Universal Login | Supported by default. |
| Classic Universal Login (no customizations) | Supported by default. |
Classic Universal Login (custom login page using Lock template lock.js widget) |
Supported if using Lock version 11.30 or higher. |
Classic Universal Login (custom login page using Custom Login Form template auth0.js widget) |
Supported if using auth0.js version 9.16 or higher to build custom login pages only if you enhance your code to handle a CAPTCHA or reCAPTCHA challenge. |
| Classic Universal Login (custom login page using Passwordless template) | Not supported. |
Web or native apps using Resource Owner Password Flow (including those using lock.android and lock.swift SDKs) |
Not supported. |
| Native apps using newest version of SDKs | Supported. The SDKs handle a risky login by invoking the Universal Login flow. |
Flows not hosted by Auth0 using lock.js, auth0.js which perform cross-origin authentication (co/authenticate endpoint) |
Not supported. |
Connection type limitations
Depending on the types of connections you use, bot detection has the following limitations.
| Connection Type | Limitation |
|---|---|
| Database | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Custom database | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Active Directory/LDAP | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Enterprise | Not supported. |
| Social Login | Not supported. |
| Passwordless | Not supported. |
Custom login page support
If you build a custom login page using Auth0.js, you can enable bot detection to render a CAPTCHA step in scenarios when a login request is determined by Auth0 to be high-risk. Your custom login form code must handle scenarios where the user is asked to pass a CAPTCHA step. To learn more, read Add Bot Detection to Custom Login Pages.
Native application support
If you build native applications using an Auth0 SDK for the login flow, you can enable bot detection to render a CAPTCHA step in scenarios when a login request is determined by Auth0 to be high-risk. Your custom login form code must handle scenarios where the user is asked to pass a CAPTCHA step. To learn more, read Add Bot Detection to Native Applications.
