Brute-Force Protection
Brute-force protection safeguards against a single IP address attacking a single user account. When a given IP address tries and fails multiple times to log in as the same user, brute-force protection:
Blocks the suspicious IP address from logging in as that user.
Sends an email to the affected user.
If an IP address is blocked due to brute-force protection, it remains blocked until one of these events occurs:
An administrator removes the block.
An administrator raises the Brute Force Threshold described below.
Thirty (30) days pass from the last failed login attempt.
The affected user selects the unblock link in the email notification (if configured).
The affected user changes their password (on all linked accounts).
Configure brute-force protection
Auth0 strongly recommends that you do not disable brute-force protection for the connection. If you disable it, you can enable it again using the Dashboard.
Go to Dashboard > Security > Attack Protection and select Brute-force Protection. Enable the toggle at the top of the page if it is disabled.
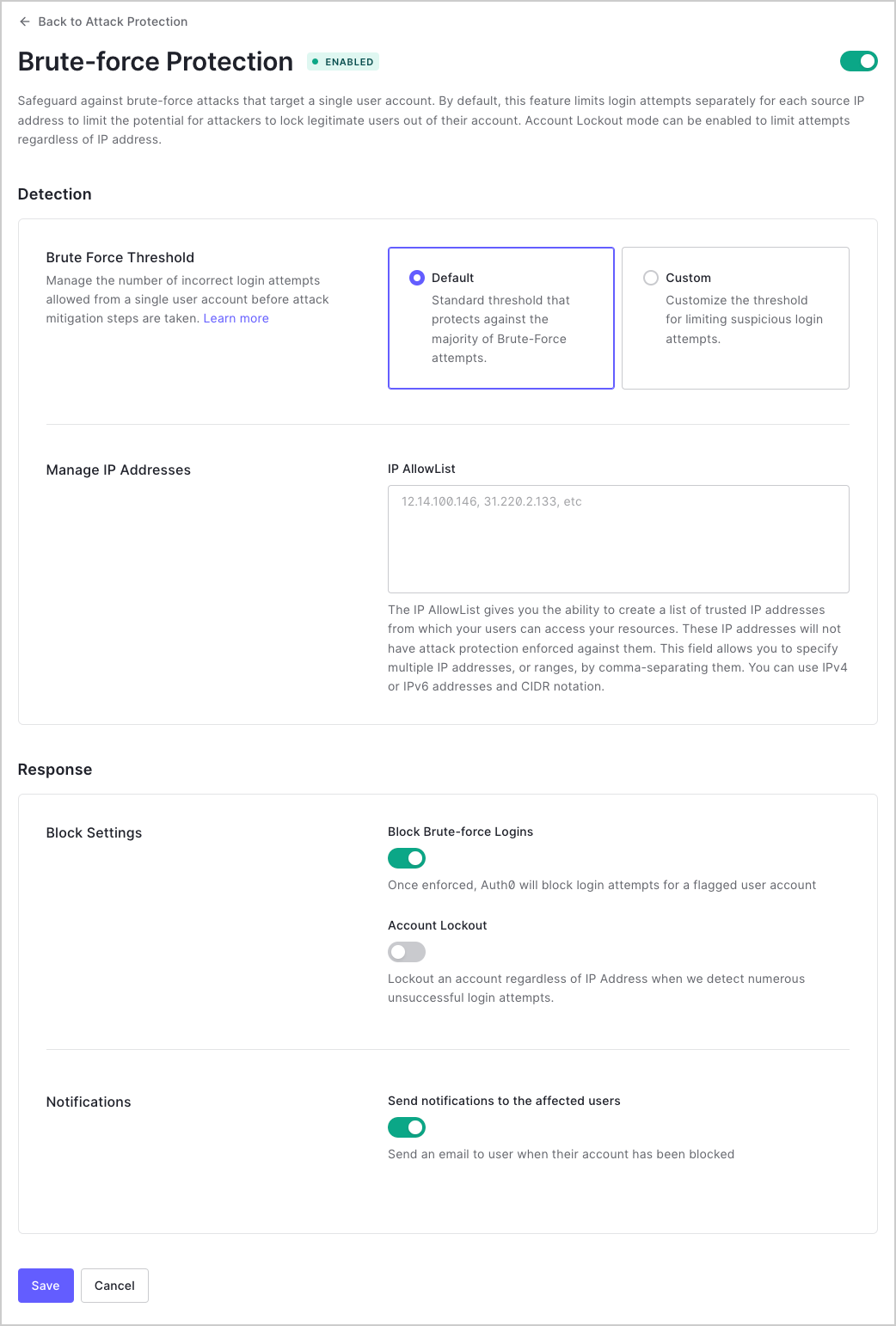
In the Detection section:
Under Brute Force Threshold, select Default to use the standard limit of 10 maximum attempts, or select Custom to set the limit of maximum attempts to a value between 1 and 100.
Under Manage IP Addresses, enter the list of trusted IP addresses in the IP AllowList field. Brute-force protection will not be enforced for login attempts originating from these IP addresses.
In the Response section:
Under Block Settings, enable the Block Brute-force Logins toggle to block attempts from suspicious IP addresses to safeguard against brute-force attacks that occur from a single IP address and target a single user account.
Under Block Settings, enable Account Lockout to trigger blocks irrespective of IP address. When this setting is enabled and a user consecutively attempts and fails to login, future attempts to log in from that user from any IP address will be blocked. You can adjust maximum attempts under Brute Force Threshold. By default, the Account Lockout toggle is disabled.
Under Notifications, enable the Send notifications to the affected users toggle to send an email notification to the user when their account has been blocked.
Click Save.
Special use cases
Because brute-force protection depends on the IP address of the user, the following use cases require additional configuration:
ROPG on the backend: Using this call does not get the IP address of the user; however, to make brute-force protection work correctly, you can configure your application and send the IP address of the user as part of the request.
User authentication from the same IP address: Users who are behind a proxy are more likely to reach set limits and trigger brute-force protection.
To learn more, read Avoid Common Issues with Resource Owner Password Flow and Attack Protection.
