Suspicious IP Throttling
Suspicious IP throttling blocks traffic from any IP address that rapidly attempts too many logins or signups. This helps protect your applications from high-velocity attacks that target multiple accounts. Suspicious IP throttling is enabled by default when you create your Auth0 tenant.
When Auth0 detects a high number of signup attempts or failed login attempts from an IP address, it suspends further attempts from that IP address. You can customize how suspicious IP throttling works for your tenant.
Enable or disable suspicious IP throttling
Auth0 strongly recommends that you do not disable suspicious IP throttling; however, you can disable and enable it from the Dashboard.
Go to Dashboard > Security > Attack Protection, and select Suspicious IP Throttling.
Select the toggle at the top-right corner of the page to turn suspicious IP throttling on or off.
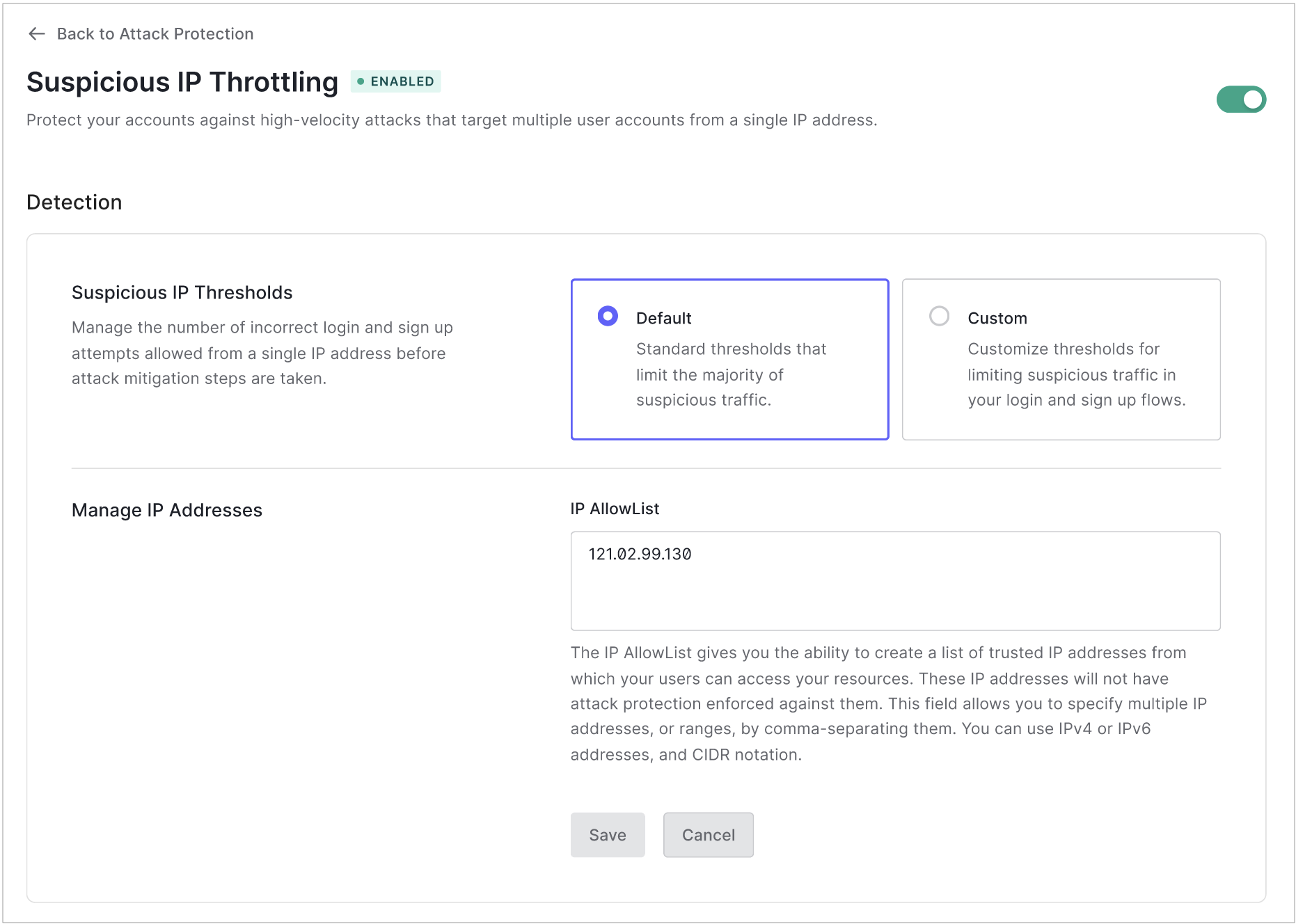
Let trusted IP addresses exceed throttling limits
You can make up to 100 certain IP addresses exempt from suspicious IP throttling by adding them to the IP Allow List. Auth0 does not block or alert when these IP addresses exceed the throttling limits.
Go to Dashboard > Security > Attack Protection, and select Suspicious IP Throttling.
In the IP AllowList box, type the IP addresses and/or CIDR ranges (IPv4 or IPv6) you want to allow unlimited login and signup attempts. Separate multiple addresses or ranges with commas.
Configure the response
By default, when an IP address exceeds the limit, Auth0 sends email to administrators and suspends attempts from the IP address as described above. You can control this response by enabling or disabling each option.
Go to Dashboard > Security > Attack Protection, and select Suspicious IP Throttling.
Under Response, choose how you want Auth0 to react to high-velocity login or signup attempts:
To control whether to throttle traffic from an IP address that exceeds the login or signup threshold, enable or disable Limit high-velocity traffic targeting too many accounts.
To control whether Auth0 sends email to administrators when an IP address exceeds the login or signup threshold, enable or disable Send notification to account administrator.
Customize throttling limits and rates
You can customize how Auth0 throttles suspicious IP addresses. You can change:
The maximum number of failed login and signup attempts that an IP address can make.
The rate at which throttled IP addresses gain new login and signup attempts.
How suspicious IP throttling works
Auth0 counts and allows login and signup attempts separately. IP addresses suspended from further login attempts can still try to sign up. IP addresses suspended from further signup attempts can still try to log in.
Login attempts
Auth0 throttles an IP address that attempts and fails too many logins in a day. The login throttling rate determines how many login attempts Auth0 grants to an IP address evenly over 24 hours. For example, a throttling rate of 100 means that Auth0 grants a new attempt approximately every 15 minutes.
Signup attempts
Auth0 throttles an IP address that attempts too many total signups in a minute. For example, if an IP address makes 50 signup attempts, Auth0 blocks further attempts. Unlike logins, the signup attempts do not need to be failures.
The signup throttling rate determines how many signup attempts Auth0 grants to an IP address evenly over 24 hours. For example, a throttling rate of 72,000 means that Auth0 grants a new attempt approximately every second.
Customize throttling
Go to Dashboard > Security > Attack Protection, and select Suspicious IP Throttling.
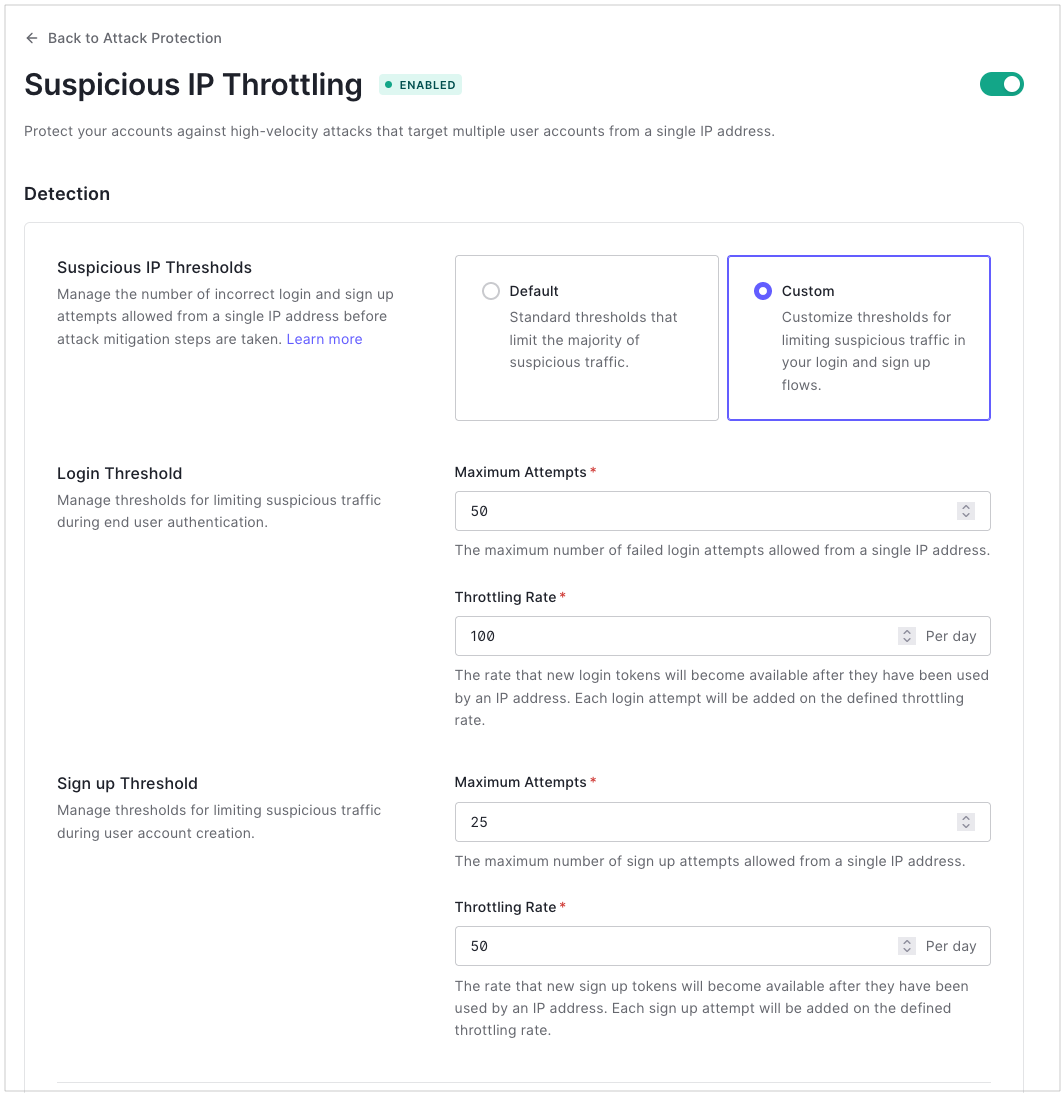
Beside Suspicious IP Thresholds, select Custom.
Locate Login Threshold.
In Maximum Attempts, set the number of failed login attempts a single IP address can make in one day before Auth0 blocks the next attempt.
In Throttling Rate, set the rate at which to grant new login tokens.
Locate Signup Threshold.
In Maximum Attempts, set the number of signup attempts a single IP address can make in one minute before Auth0 blocks the next attempt.
In Throttling Rate, set the rate at which to grant new signup tokens.
Special cases
Because suspicious IP throttling depends on the IP address of the user, the following use cases require additional configuration:
Using the Resource Owner Password Grant from the backend of an application: Using this call does not get the IP address of the user; however, to make suspicious IP throttling work correctly, you can configure your application to send the IP address of the user as part of the request. See Avoid Common Issues with Resource Owner Password Flow and Attack Protection: Send the user's IP address from your server.
Authenticating a large number of users from the same IP address: Users who are behind a proxy are more likely to reach set limits and trigger throttling. You can avoid erroneously triggering throttling by configuring an AllowList for the proxy's IP and CIDR range. See Avoid Common Issues with Resource Owner Password Flow and Attack Protection: Configure your Application to trust the IP address.
