Enable Multi-Factor Authentication
You can enable MFA and choose the factors (such as push notifications or SMS) you want to use with your tenant in the Auth0 Dashboard. After you complete any further steps required to configure specific factors, you define a policy for when users will be prompted to complete additional authentication steps.
You can also customize your MFA flow using Auth0 rules to require MFA in specific circumstances or force a particular factor to be used. To learn more, read Customize Adaptive MFA with Rules and Sample Use Cases: Rules with Authorization.
Go to Dashboard > Security > Multi-factor Auth.
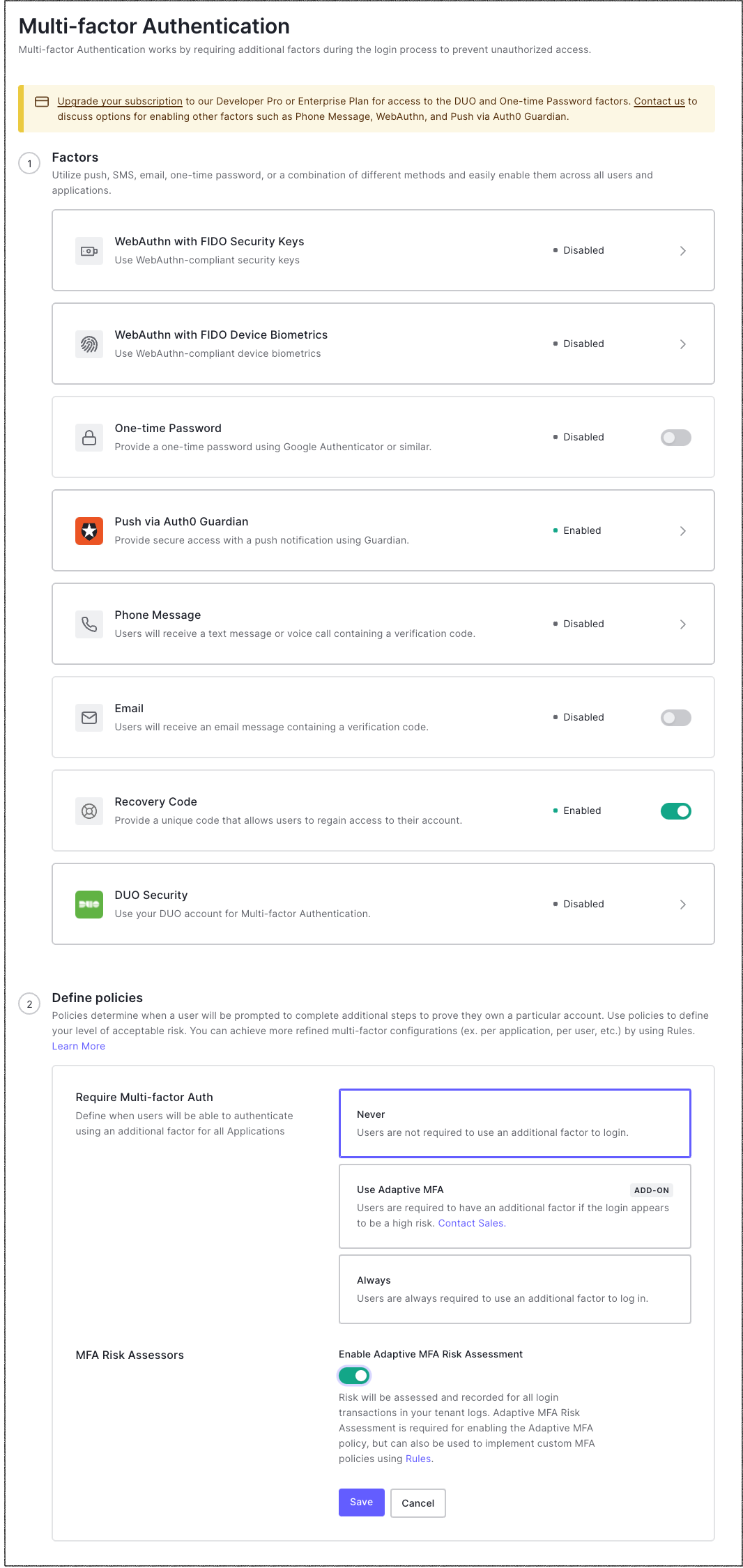
In the Factors section, choose the factors that you want to enable with toggles. Any or all of these factors can be enabled simultaneously. When logging in the first time, the user will be shown the most secure factor available but will be allowed to choose another factor to use if you have more than one factor enabled in the Dashboard. The SMS and Cisco Duo factors require further configuration. Click on the factor and configure settings before continuing.
In the Define policies section, next to Require Multi-factor Auth, choose a policy to determine when users will be prompted to complete additional steps to prove that they own a particular account. Use policies to define your level of acceptable risk.
Never: MFA is not triggered for any logins.
Use Adaptive MFA: MFA is triggered based on Auth0 risk determination. To learn more, read Enable Adaptive MFA.
Always: MFA is always triggered for all logins. Users will be able to use any of the factors enabled in the Dashboard.
If you choose Never or Always as the policy, the MFA Risk Assessors section appears. By default, the Enable Adaptive MFA Risk Assessment toggle is disabled. In this mode, risk will not be assessed or recorded in your tenant logs. Enable the toggle to assess risk and record events.
Click Save.
