Configure Cisco Duo Security for MFA
Cisco Duo is a multi-faceted authentication provider and can only be used on your Auth0 tenant if all other factors are disabled. Your Duo account can support push notifications, SMS, OTP, phone callback, and more based on your configuration.
You cannot also enable Duo if other factors are enabled. Duo is only available to users when it is the sole factor enabled.
The application will prompt the user for the second factor with Duo, listing the options you have enabled in your Duo account.
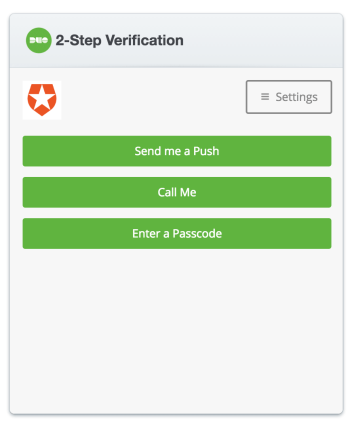
Your users can download Duo from Google Play or the App Store for use as a second factor.
Prerequisites
If you have not configured your Duo account, get started with the Duo documentation.
Create a Duo Security Web SDK integration and capture the Integration Key, Secret Key, and API hostname credentials.
Configure Duo
To configure Duo Security, you must pass your Duo credentials to your application in the Auth0 Dashboard.
Go to Dashboard > Security > Multi-factor Auth > Duo Security and enable it.
Enter the information in the fields to link your Duo account to Auth0.
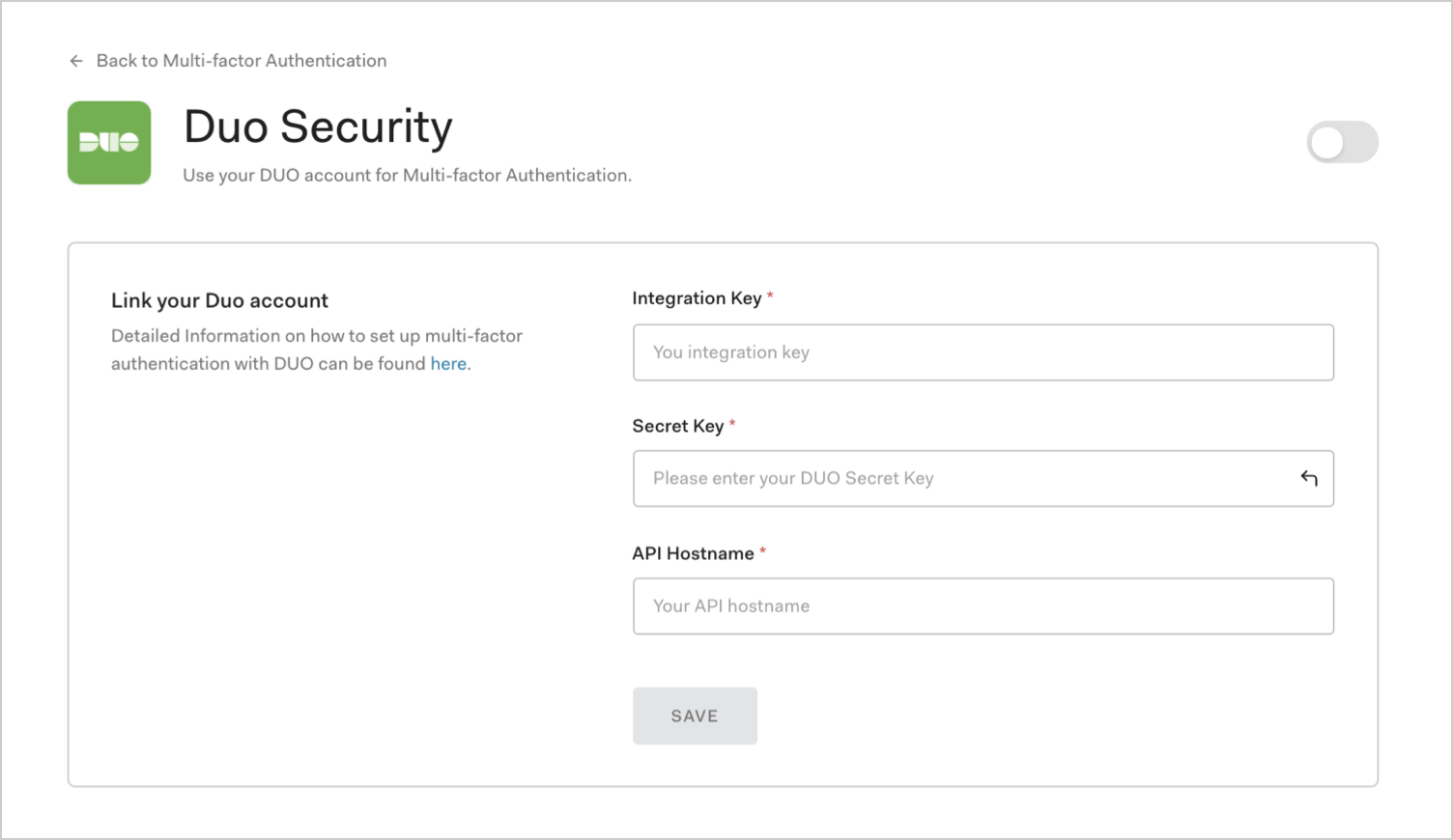
Click Save.
Enabling Duo from Rules
If you want to enable Duo from Rules, add set provider : 'duo' to your function.
function (user, context, callback) {
context.multifactor = {
provider: 'duo',
allowRememberBrowser: false
};
callback(null, user, context);
}Was this helpful?
Duo does not provide an option for "Remember Me" behavior. The 30-day MFA session is hard-coded to remember the user after the initial login.
To force your users to log in with Duo every time, create a rule with allowRememberBrowser: false.
Current Limitations
You cannot use Auth0 MFA Enrollment Tickets to enroll users with Duo. Onboard those users from Duo itself.
If you use New Universal Login, you must enable Duo from a rule with
provider:'duo'as described above. You can conditionally use Duo or the built-in Auth0 provider for specific applications.
